Learning Outcomes
By the end of this session the student should be able to describe the OSI model and compare/relate its structure and layer functions to other communications protocols. The communications protocols that the student shoud be able to compare include: OSI, TCP/IP, and SNA.
Introduction
The concepts of distributed processing and computer
networking imply that entities in different systems need to communicate. Examples of
entities are user application programs, file transfer packages, database management
systems, electronic mail facilities and terminals. Examples of systems are computers,
terminals and remote sensors. In general an entity is anything capable of sending and
receiving information, and a system is a physically distinct object that contains one or
more entities.
For two entities to communicate they must speak the same language. What is communicated, how it is communicated and when it is communicated must conform to some mutually acceptable set of conventions. The set of conventions is referred to as a protocol, which is defined as a set of rules governing the exchange of data between two entities. The key elements of a protocol are:
The OSI Model
As the use of computer communications and computer networks proliferates, a
one-at-a-time special purpose approach to communication software development is too costly
to be acceptable. The only alternative is for computer vendors to adopt and implement a
common set of conventions. For this to happen a set of international standards must be
promulgated by appropriate organisations. Such standards have two effects:
This line of reasoning lead to the International Organisation for Standardisation in 1977 to establish a sub-committee to develop such an architecture. The result was OSI (Open Systems Interconnect) reference model, adopted in 1983 as a framework for developing standards for linking heterogeneous computers.
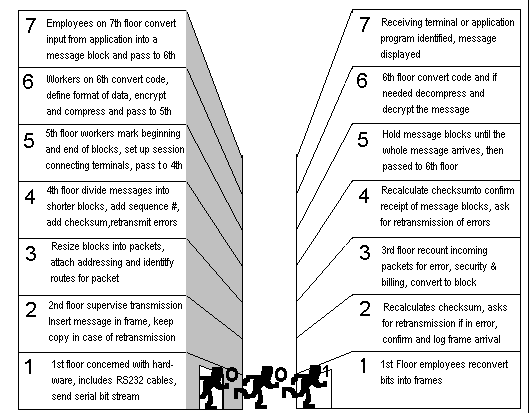
A widely accepted structuring technique is layering, in which communication functions are partitioned into a vertical set or layer. Each layer performs a related subset of function required to communicate with another system. It relies on the next lower layer to perform more primitive functions and to conceal details of these functions. It provides services to the next higher layer.
The task of the ISO sub-committee was to define a set of layers and services performed by each layer. The resulting OSI model has seven layers.
Note that there is no communications between peer levels except at the physical layer.
The Physical Layer
The physical layer is concerned primarily with
transmitting data bits over a communication circuit. The main purpose of this layer is to
define the rules by which one side sends a 1 bit so that the other side knows that it is a
1 bit when it is received. The physical layer covers the physical interface between
devices and the rules by which bits are passed to each other. the devices include computer
and terminals and are generically referred to as data terminal equipment (DTE). The DTE
makes use of the transmission system through the mediation of data circuit-terminating
equipment (DCE), an example of this is a modem. The physical layer has four important
characteristics:
Examples of standards at this layer are EIA-232-D, EIA-530.
The Data-Link Layer
The data link layer attempts to make the physical
link reliable and provides the means to activate , maintain and deactivate a link. The
principal service provided by the data link layer is that of error correction and control.
It is the task of the data link layer to create and recognise frame boundaries and check
for errors during transmission.
Examples of standards at this level are X.25, HDLC, ADLCP and LAP-B.
The Networkl Layer
The basic service of the network layer is to
provide for the transparent transfer of data between transport entities. The network
service is responsible for establishing, maintaining and terminating connections across
the intervening communications facility. This layer provides the services that move data
through the network to its destination node/terminal. Routing of packets is another task
of this layer, packet routing also involves load-leveling the volume of transmissions
through any circuit.
The best example of network protocols is X.25.
The Transportl Layer
Layers 4 and above of the OSI model are generally
referred to as the higher levels. Protocols at these levels are end-to-end and are not
concerned with the details of the underlying communications facility.
The purpose of layer 4 is to provide a reliable mechanism for the exchange of data between processes in different systems. The transport layer ensures that units are delivered error free, in sequence, with no loss or duplications. The transport layer may also be concerned with optimising the use of network services.
The Session Layer
The session layer provides the mechanism for
controlling dialogue between applications. At a minimum, the session layer provides a
means for two application processes to establish and use a connection called a session. In
addition it may also provide the following services:
- dialogue type; can be two-way simultaneous, two-way alternate or one-way.
- recovery; the session layer can provide a checkpointing mechanism, so that if a failure occurs between checkpoints, the session entity can retransmit all the data since the last checkpoint.
The Presentation Layer
The presentation layer is concerned with the syntax
of the data exchanged between application entities. Its purpose is to resolve differences
in format and data representation. The presentation layer defines the syntax used between
application entities.
Examples of presentation protocols are encryption and virtual terminal protocols.
The Application Layer
The application layer provides the means for
applications to access the OSI environment. This layer contains management functions and
generally useful mechanisms to support distributed applications.

The TCP/IP Model
The Transmission Control Protocol/Internet Protocol (TCP/IP) probably is the
oldest networking standard, developed for the U.S. Department of Defense’s Advanced
Research Project Agency NETwork (ARPANET) in the 1970s. It is also the most popular
network, used by more than 50% of all installed backbone, metropolitan, and wide area
networks. TCP/IP is also the network protocol used on the Internet. TCP/IP allows
reasonably efficient and error free transmission between different systems. Because it is
a file transfer protocol, it can send large files of information across sometimes
unreliable networks with great assurance that the message will arrive uncorrupted. TCP/IP
is also compatible with a large variety of data link protocols, which one reason for its
popularity. In a 1995 survey of IT managers, 79% said that TCP/IP was critical to their
future plans, and a further 18% said it was important.
As the name implies, TCP/IP has two parts. TCP performs the functions of the transport layer in OSI (breaking data into smaller packets, numbering them, ensuring each packet is reliably delivered, and putting them in proper order). IP performs the role of the network layer (routing and addressing). IP is used at each of the intervening computers through which the messsage passes; it is IP that routes the message to its final destination. IP can be either static routing (RIP) or dynamic routing (OSPF) to make routing decisions.

TCP/IP can operate as either a connection-oriented or connectionless. TCP is inherently connectionless. When connection-oriented routing is desired, both TCP and IP are used; when connectionless routing is required only IP is used and TCP is bypassed. However since TCP is bypassed, the application layer must perform the functions of TCP (ensuring that all the packets reach the destination in the correct order). Connectionless routing is commonly used when the application data or message can fit into one packet.
A typical TCP packet has a 192-bit header of control information. Among other fields, it contains the source and destination, packet sequence number, and error checking information.

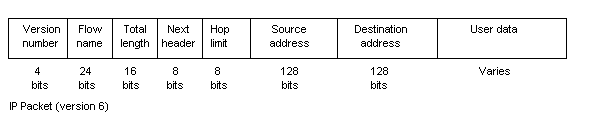
Two forms of IP are currently in use. The older form IP version 4 (IP4), which also has a 192-bit header. This header contains source and destination address, packet length and packet number. IP4 is being displaced by IP6, which has a 320-bit header. The primary reason for the increase is the increase in address size from 32 bits to 128 bits. This has been brought about by the dramatic growth in the Internet.
TCP/IP will supoort a variety of data link protocols, but is typically combined with Ethernet. The maximum amount of application data that can be sent in one packet depends on the data link protocol used.
The SNA Model
When IBM introduced Systems Network Architecture (SNA), its strategic wide
area networking product family, in 1974, mainframes dominated computer environments.
Because they were ruled by mainframes, the computer networks in use were hierarchical, or
tree-structured, with the mainframe at the top of the inverted tree. This arrangement
required lower-level systems on the network to communicate with each other through the
mainframe rather than directly with each other, which was a tremendous waste of host-based
resources.
The popularity of personal computers in the 1980s changed the structure of corporate computing, however, No longer were computing resources located in or controlled from a centralized location: They were now distributed throughout an organization, in dozens (even hundreds) of PCs as well as the mainframe.
The growth of PC-based networks further strengthened this distributed environment. With hundreds of PCs connected to networks— needing to communicate with each other— became intolerable for most organizations to rely solely on the traditional SNA-type network. No longer could they allocate host resources to managing communication among the dozens of computers on the network.
In 1982, IBM responded by adding a protocol called Logical Unit (LU) 6.2 to SNA. LU6.2 makes all computers peers on an SNA network, including hosts. With LU6.2, the mainframe no longer plays dictator to its “” counterparts on the network. LU6.2 brought other changes to SNA as well. Rather than forcing devices connected to SNA to act as dumb terminals incapable of handling processing, LU6.2 permits cooperative processing. Each processor on the network can do what it does best rather than rely on the mainframe. It also allows the dynamic allocation and tuning of SNA networks, substantially reducing the need for operator intervention.
Structure
SNA, with IBM’ market presence behind it, has
been a de facto data processing and networking standard for many years. IBM has developed
and installed sufficient hardware and software to make SNA the world’ most widely
installed network topology, with more than 22,000 sites.
As a protocol suite, SNA offers functionality similar (and is an alternative) to the Transmission Control Protocol/Internet Protocol (TCP/IP) and Open Systems Interconnection (OSI) protocols. Like these protocols, SNA offers a layered approach to communications. From the top down, SNA’ seven layers are: end-user, network-addressable unit services, data flow control, transmission flow control, path control, data link control, and physical layers. Together, they provide services that are more or less synonymous with those of OSI and TCP/IP. However, the layers’ functions do not completely correspond from one protocol to another.
These layers handle the following tasks. The physical layer (layer 1) moves data between computers on a network. The data-link layer (layer 2) uses the Synchronous Data Link Control (SDLC) protocol to pass data across the physical interface. The path control layer (layer 3) manages routing and traffic control, packing data together to increase throughput. The transmission control layer (layer 4) initiates, manages, and concludes transport connections or sessions, controlling the data-flow rate between layers 3 and 5. The data-flow control layer (layer 5) determines which LU can transmit next and helps manage error recovery. The NAU services layer (layer 6) handles presentation services to layer 7. The end-user layer (layer 7) provides the user interface.
LU and PU Functions
Logical units (or LUs) and physical units (PUs) are
the two primary functional entities in an SNA network. Both LUs and PUs are also referred
to as network-addressable units (NAUs).
In SNA parlance, PUs are physical systems or nodes connected to each other via cabling. PUs are also known as Node Types, or NTs. IBM has defined five node types, including hosts (PU5) and terminals (PU2), and left a sixth available for future definition. For the sake of simplicity, we’ refer to node types/physical units only with the PU designation— as PU2.0— it’ just as accurate to label PU2.0 as NT2.0.
Logical units are electronic entities connected by sessions. Just as there are five PUs, there are five LUs, including LU6.2, that make SNA network resources, including disk files and processing cycles, available for application software. A node on an SNA network can be a physical unit (such as hardware) as well as a logical unit (such as a logical session connection).
In essence, LU6.2 acts as an interface, or protocol boundary, between SNA and an end user’ application. Closely associated with LU6.2 is PU (or node type) 2.1, which is an enhancement to PU2.0 for cluster controllers. PU2.0, also known as 3270 terminal emulation, is the protocol most often used to connect personal computers into an SNA network. PU2.0 also lets other devices on an SNA network access a mainframe by emulating a cluster controller.
PU2.0 has some limitations, however. Most importantly, it allows devices to access only a host, not other peer nodes. And it requires one or more System Service Control Points (SSCP), which start and stop sessions. PU2.1 remedies these shortcomings.
PU2.1 includes all the features of PU2.0, with major upgrades. It allows SNA devices to connect to peer nodes without mainframe assistance, and it permits running multiple sessions simultaneously. And while PU2.0 permits only peripheral node connections, PU2.1 provides peer-to-peer connectivity. PU2.1 also requires no central control point to manage session services.
LU and PU Types
There are five LUs and an identical number of PUs.
We’ described one of each already. The table provides a brief description of the full
set of physical and logical units.
Of the logical and physical units listed in the table, LU3 is outdated. LU6.2, which can be considered a subset of SNA, consists of a base set of features plus 41 options. IBM implements LU6.2 across its entire product line, although the specifics vary from product to product. In its most popular form, users know LU6.2 as Advanced Program-to-Program Communication (APPC).
Users purchase APPC in the form of a developer’ toolkit, which allows them to create transaction programs capable of using entities called APPC verbs. These APPC verbs are used within the transaction program to get LU6.2/APPC to perform functions the program needs carried out. Although APPC and LU6.2 are synonymous, their verb names differ slightly. With a few exceptions— example, APPC/PC does not support some of the more obscure features of LU6.2— functionality is virtually identical to that of LU6.2.
LU6.2/APPC functions primarily as a resource allocator and controller. This means that LU6.2/APPC ensures that programs have access to network resources when they need them, and that network resources are not corrupted, such as when two users attempt to make simultaneous updates to the same file.
IBM has made APPC its preferred LU6.2 implementation in a variety of its systems, including its PCs, System/38/36, AS/400, and 9370 mainframe. IBM has said that APPC is its strategic product for distributed processing in the minicomputer and PC environments. IBM sees APPC as one way of taking PC-to- mainframe market share away from terminal emulation applications.
On the PC Side
APPC/PC is IBM’ offering at the low end of the
LU6.2 market. Two versions are available. Version 1.1 is designed for IBM’ Token Ring
and PC LAN Program networks and stand-alone micros. The OS/2 Extended Edition APPC is part
of the Communications Manager for OS/2.
While backed by IBM, the memory-resident APPC/PC program has met resistance from end users. It consumes 164 KB of RAM, which is too much for most PC users to spare. With only 640 KB of DOS-addressable memory, many users don’ have enough RAM to run DOS, APPC/PC, and applications software on a network. This is not an issue for end users running OS/2, which can access up to 16MB of memory; however, only a small percentage of users in the PC environment are using OS/2.
Because of the memory limitation, third-party applications developers have been slow to release software that takes advantage of APPC/PC. If more users migrate to OS/2, developers are likely to release more applications written to APPC/PC.
Another of IBM’ LU6.2 implementations is Advanced Peer-to-Peer Networking (APPN). APPN adds network management capabilities to LU6.2 peer-to-peer communications services. APPN also includes a routing capability that can create new routes between nodes on a network dynamically.